n2n
n2n
a Layer Two Peer-to-Peer VPN
n2n is a layer-two peer-to-peer virtual private network (VPN) which allows users to exploit features typical of P2P applications at network instead of application level. This means that users can gain native IP visibility (e.g. two PCs belonging to the same n2n network can ping each other) and be reachable with the same network IP address regardless of the network where they currently belong. In a nutshell, as OpenVPN moved SSL from application (e.g. used to implement the https protocol) to network protocol, n2n moves P2P from application to network level.
The main n2n design features are:
- An n2n is an encrypted layer two private network based on a P2P protocol.
- Encryption is performed on edge nodes using open protocols with user-defined encryption keys: you control your security without delegating it to companies as it happens with Skype or Hamachi.
- Each n2n user can simultaneously belong to multiple networks (a.k.a. communities).
- Ability to cross NAT and firewalls in the reverse traffic direction (i.e. from outside to inside) so that n2n nodes are reachable even if running on a private network. Firewalls no longer are an obstacle to direct communications at IP level.
- n2n networks are not meant to be self-contained, but it is possible to route traffic across n2n and non-n2n networks.
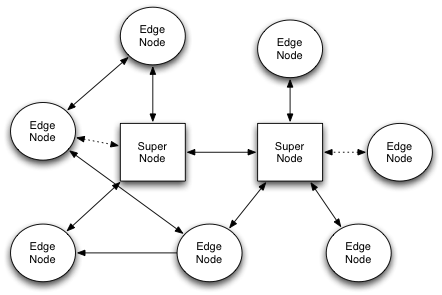
The n2n architecture is based on two components:
- edge nodes: applications installed on user PCs that allow the n2n network to be build. Practically each edge node creates a tun/tap device that is then the entry point to the n2n network.
- an supernode: it is used by edge nodes at startup or for reaching nodes behind symmetrical firewalls. This application is basically a directory register and a packet router for those nodes that cannot talk directly.
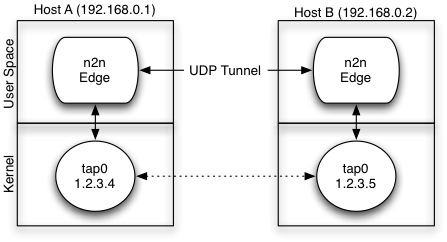
Edge nodes talk by means of virtual tap interfaces. Each tap interface is an n2n edge node. Each PC can have multiple tap interfaces, one per n2n network, so that the same PC can belong to multiple communities.
Quickstart
- Download and compile the code
- Decide where to place your supernode. Suppose you put it on host a.b.c.d at port xyw.
- Decide what encryption password you want to use to secure your data. Suppose you use the password encryptme
- Decide the network name you want to use. Suppose you call it mynetwork. Note that you can use your supernode/edge nodes to handle multiple networks, not just one.
- Decide what IP address you plan to use on your edge nodes. Suppose you use IP address 10.1.2.0/24
- Start your applications:
-
#supernode > supernode -l xyw
#edge node1> edge -a 10.1.2.1 -c mynetwork -k encryptme -l a.b.c.d:xyw
#edge node2> edge -a 10.1.2.2 -c mynetwork -k encryptme -l a.b.c.d:xywNow test your n2n network:
#edge node1> ping 10.1.2.2
#edge node2> ping 10.1.2.1
only.hk n2n server setting
Server : only.hk
Port : 1688
Linux’s connection script :
edge -a 10.10.10.20 -c vpn -k 1234 -l only.hk:1688
Windows’s Connection Using n2ngui n2nguien
